AI tools for cyber job matching for remote work
Related Tools:

JobWharf.ai
JobWharf.ai is an AI-powered job application platform that helps users apply for jobs by submitting their CVs to various companies and startups. The platform offers a wide range of job opportunities in different categories and regions, with features like refining job searches, sending job applications on behalf of users, and providing CV optimization services. JobWharf.ai aims to simplify the job hunting process and increase users' chances of getting hired by matching their career goals with suitable employment opportunities.

Simplilearn
Simplilearn is an online bootcamp and certification platform that offers courses in various fields, including AI and machine learning, project management, cyber security, cloud computing, and data science. The platform partners with leading universities and companies to provide industry-relevant training and certification programs. Simplilearn's courses are designed to help learners develop job-ready skills and advance their careers.

STR
STR is a technology company that develops and applies artificial intelligence to solve emerging national security challenges. The company's mission is to make the world a safer place by using AI to protect citizens from oppressive governments and other threats. STR's team is made up of motivated and creative people who are passionate about using their skills to make a difference in the world.
CYBER AI
CYBER AI is a security report savant powered by DEPLOYH.AI that simplifies cybersecurity for businesses. It offers a range of features to help organizations understand, unlock, and uncover security threats, including security reports, databreach reports, logs, and threat hunting. With CYBER AI, businesses can gain a comprehensive view of their security posture and take proactive steps to mitigate risks.
Stellar Cyber
Stellar Cyber is an AI-driven unified security operations platform powered by Open XDR. It offers a single platform with NG-SIEM, NDR, and Open XDR, providing security capabilities to take control of security operations. The platform helps organizations detect, correlate, and respond to threats fast using AI technology. Stellar Cyber is designed to protect the entire attack surface, improve security operations performance, and reduce costs while simplifying security operations.
Cybrary
Cybrary is an AI-focused platform that offers a wide range of resources and information related to artificial intelligence, machine learning, big data, cybersecurity, and more. It covers various industries such as banking, finance, healthcare, education, and provides insights on emerging technologies like generative AI, enterprise AI, and blockchain. The platform features articles, guides, and tutorials on cutting-edge AI technologies, with a focus on practical applications and industry-specific use cases.
Cyble
Cyble is a leading threat intelligence platform offering products and services recognized by top industry analysts. It provides AI-driven cyber threat intelligence solutions for enterprises, governments, and individuals. Cyble's offerings include attack surface management, brand intelligence, dark web monitoring, vulnerability management, takedown and disruption services, third-party risk management, incident management, and more. The platform leverages cutting-edge AI technology to enhance cybersecurity efforts and stay ahead of cyber adversaries.
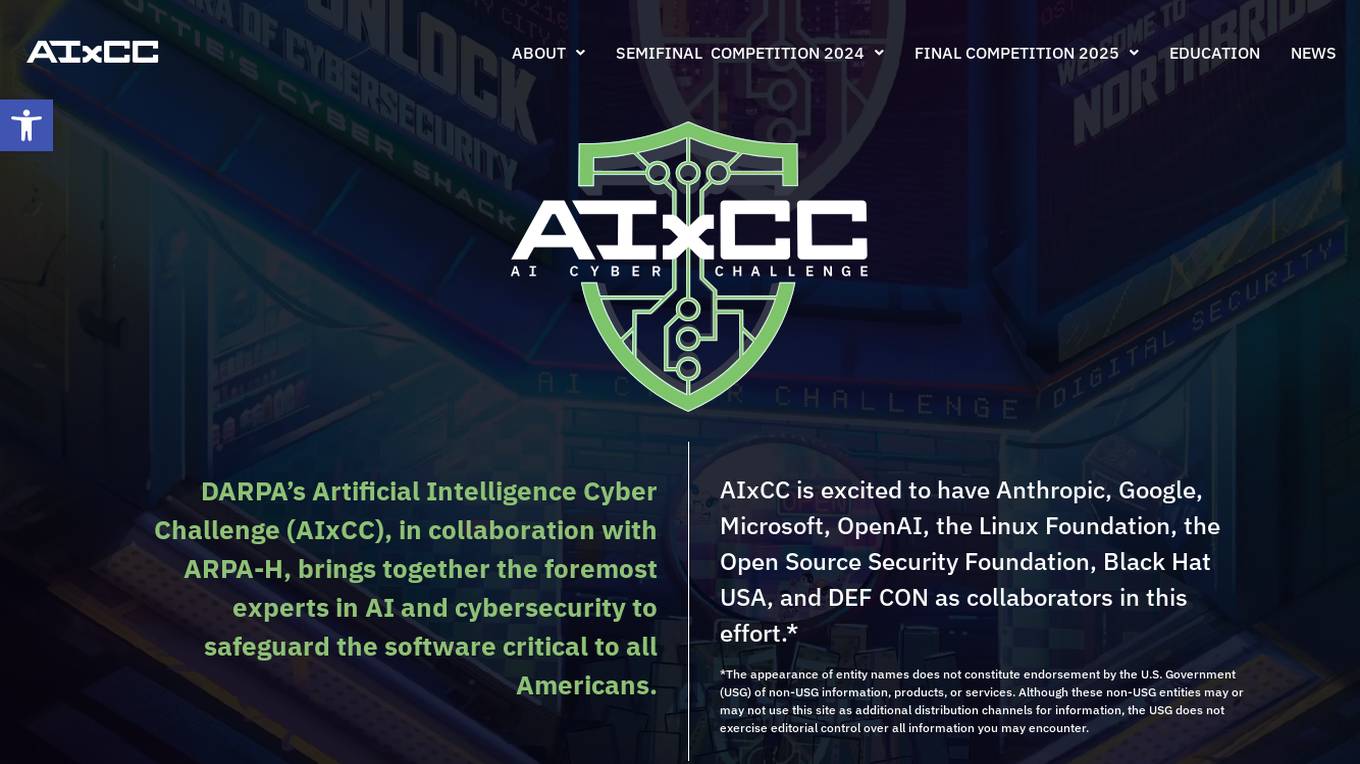
DARPA's Artificial Intelligence Cyber Challenge (AIxCC)
The DARPA's Artificial Intelligence Cyber Challenge (AIxCC) is an AI-driven cybersecurity tool developed in collaboration with ARPA-H and various industry experts like Anthropic, Google, Microsoft, OpenAI, and others. It aims to safeguard critical software infrastructure by utilizing AI technology to enhance cybersecurity measures. The tool provides a platform for experts in AI and cybersecurity to come together and address the evolving threats in the digital landscape.
Darktrace
Darktrace is a cybersecurity platform that leverages AI technology to provide proactive protection against cyber threats. It offers cloud-native AI security solutions for networks, emails, cloud environments, identity protection, and endpoint security. Darktrace's AI Analyst investigates alerts at the speed and scale of AI, mimicking human analyst behavior. The platform also includes services such as 24/7 expert support and incident management. Darktrace's AI is built on a unique approach where it learns from the organization's data to detect and respond to threats effectively. The platform caters to organizations of all sizes and industries, offering real-time detection and autonomous response to known and novel threats.
Darktrace
Darktrace is an essential AI cybersecurity platform that offers proactive protection, cloud-native AI security, comprehensive risk management, and user protection across various devices. It accelerates triage by 10x, defends with confidence, and connects with various integrations. Darktrace ActiveAI Security Platform spots novel threats across organizations, providing solutions for ransomware, APTs, phishing, data loss, and more. With a focus on defense, Darktrace aims to transform cybersecurity by detecting and responding to known and novel threats in real-time.
Alston & Bird Privacy, Cyber & Data Strategy Blog
Alston & Bird Privacy, Cyber & Data Strategy Blog is an AI tool that provides insights and updates on key data privacy, cybersecurity issues, and regulations. The blog covers a wide range of topics such as COPPA Rule amendments, AI advisory in healthcare, DHS Playbook for AI deployment, cybersecurity sanctions, and data breach notification laws. It aims to keep readers informed about the latest developments in privacy, cyber, and data strategy.
E-commerce Store
The website is currently unavailable, indicating that the store is temporarily closed and awaiting restoration by the store owner. It seems to be a simple e-commerce store that is not operational at the moment.
CUBE3.AI
CUBE3.AI is a real-time crypto fraud prevention tool that utilizes AI technology to identify and prevent various types of fraudulent activities in the blockchain ecosystem. It offers features such as risk assessment, real-time transaction security, automated protection, instant alerts, and seamless compliance management. The tool helps users protect their assets, customers, and reputation by proactively detecting and blocking fraud in real-time.
CyberUpgrade
CyberUpgrade.net is an AI-powered platform that offers comprehensive cybersecurity and compliance solutions for organizations of all sizes. It provides automated compliance, risk management, vendor risk assessment, policy management, audit management, and 24/7 security support. The platform features a cloud vulnerability scanner, security awareness training, pentesting, business continuity planning, disaster recovery planning, and an AI-powered assistant for seamless security support. CyberUpgrade helps CTOs understand their organization's security status, proposes improvement plans, guides execution, and prepares compliance documentation with a push of a button. It engages every employee individually for evidence collection and situation analysis, ensuring real cybersecurity measures are in place.
SANS AI Cybersecurity Hackathon
SANS AI Cybersecurity Hackathon is a global virtual competition that challenges participants to design and build AI-driven solutions to secure systems, protect data, and counter emerging cyber threats. The hackathon offers a platform for cybersecurity professionals and students to showcase their creativity and technical expertise, connect with a global community, and make a real-world impact through AI innovation. Participants are required to create open-source solutions addressing pressing cybersecurity challenges by integrating AI, with a focus on areas like threat detection, incident response, vulnerability scanning, security dashboards, digital forensics, and more.
Vectra AI
Vectra AI is an advanced AI-driven cybersecurity platform that helps organizations detect, prioritize, investigate, and respond to sophisticated cyber threats in real-time. The platform provides Attack Signal Intelligence to arm security analysts with the necessary intel to stop attacks fast. Vectra AI offers integrated signal for extended detection and response (XDR) across various domains such as network, identity, cloud, and endpoint security. Trusted by 1,500 enterprises worldwide, Vectra AI is known for its patented AI security solutions that deliver the best attack signal intelligence on the planet.
Spin.AI
Spin.AI is an AI-powered SaaS security platform that provides full visibility and control over mission-critical applications. With features such as SSPM, DSPM, ransomware detection & response, data leak prevention, and backup & disaster recovery, Spin.AI offers comprehensive protection for SaaS data. Trusted by over 1,500 organizations across 100+ countries, Spin.AI helps enhance cyber resilience, security operations, and cost efficiency for businesses.

Fathom5
Fathom5 is a company that specializes in the intersection of AI and industrial systems. They offer a range of products and services to help customers build the industrial systems of the future. Their solutions are focused on critical infrastructure, making it more resilient, flexible, and efficient.
Attestiv
Attestiv is an AI-powered digital content analysis and forensics platform that offers solutions to prevent fraud, losses, and cyber threats from deepfakes. The platform helps in reducing costs through automated photo, video, and document inspection and analysis, protecting company reputation, and monetizing trust in secure systems. Attestiv's technology provides validation and authenticity for all digital assets, safeguarding against altered photos, videos, and documents that are increasingly easy to create but difficult to detect. The platform uses patented AI technology to ensure the authenticity of uploaded media and offers sector-agnostic solutions for various industries.
Cyber Test & CareerPrep
Helping you study for cybersecurity certifications and get the job you want!
Cyber Threat Intelligence
An automated cyber threat intelligence expert configured and trained by Bob Gourley. Pls provide feedback. Find Bob on X at @bobgourley
Cyber Shielder
Expert in cyber security (NIST, OWASP, NIS2, MITRE ATT&CK, DORA) and GDPR, offering clear and concise guidance.
CISO AI
Team of experts assisting CISOs, CIOs, Exec Teams, and Board Directors in cyber risk oversight and security program management, providing actionable strategic, operational, and tactical support. Enhanced with advanced technical security architecture and engineering expertise.
AI Cyberwar
AI and cyber warfare expert, advising on policy, conflict, and technical trends
EU CRA Assistant
Expert in the EU Cyber Resilience Act, providing clear explanations and guidance.
Jordan Cipher
Your guide through the digital frontier, unveiling cyber secrets with expertise.
Black Friday Cyber Monday - Deal Guide 2023
Comprehensive Black Friday/Cyber Monday shopping and budgeting advisor
T71 Russian Cyber Samovar
Analyzes and updates on cyber-related Russian APTs, cognitive warfare, disinformation, and other infoops.
CyberNews GPT
CyberNews GPT is an assistant that provides the latest security news about cyber threats, hackings and breaches, malware, zero-day vulnerabilities, phishing, scams and so on.
AITreasureBox
AITreasureBox is a comprehensive collection of AI tools and resources designed to simplify and accelerate the development of AI projects. It provides a wide range of pre-trained models, datasets, and utilities that can be easily integrated into various AI applications. With AITreasureBox, developers can quickly prototype, test, and deploy AI solutions without having to build everything from scratch. Whether you are working on computer vision, natural language processing, or reinforcement learning projects, AITreasureBox has something to offer for everyone. The repository is regularly updated with new tools and resources to keep up with the latest advancements in the field of artificial intelligence.

awesome-and-novel-works-in-slam
This repository contains a curated list of cutting-edge works in Simultaneous Localization and Mapping (SLAM). It includes research papers, projects, and tools related to various aspects of SLAM, such as 3D reconstruction, semantic mapping, novel algorithms, large-scale mapping, and more. The repository aims to showcase the latest advancements in SLAM technology and provide resources for researchers and practitioners in the field.
awesome-business-of-cybersecurity
The 'Awesome Business of Cybersecurity' repository is a comprehensive resource exploring the cybersecurity market, focusing on publicly traded companies, industry strategy, and AI capabilities. It provides insights into how cybersecurity companies operate, compete, and evolve across 18 solution categories and beyond. The repository offers structured information on the cybersecurity market snapshot, specialists vs. multiservice cybersecurity companies, cybersecurity stock lists, endpoint protection and threat detection, network security, identity and access management, cloud and application security, data protection and governance, security analytics and threat intelligence, non-US traded cybersecurity companies, cybersecurity ETFs, blogs and newsletters, podcasts, market insights and research, and cybersecurity solutions categories.
Awesome_GPT_Super_Prompting
Awesome_GPT_Super_Prompting is a repository that provides resources related to Jailbreaks, Leaks, Injections, Libraries, Attack, Defense, and Prompt Engineering. It includes information on ChatGPT Jailbreaks, GPT Assistants Prompt Leaks, GPTs Prompt Injection, LLM Prompt Security, Super Prompts, Prompt Hack, Prompt Security, Ai Prompt Engineering, and Adversarial Machine Learning. The repository contains curated lists of repositories, tools, and resources related to GPTs, prompt engineering, prompt libraries, and secure prompting. It also offers insights into Cyber-Albsecop GPT Agents and Super Prompts for custom GPT usage.

Academic_LLM_Sec_Papers
Academic_LLM_Sec_Papers is a curated collection of academic papers related to LLM Security Application. The repository includes papers sorted by conference name and published year, covering topics such as large language models for blockchain security, software engineering, machine learning, and more. Developers and researchers are welcome to contribute additional published papers to the list. The repository also provides information on listed conferences and journals related to security, networking, software engineering, and cryptography. The papers cover a wide range of topics including privacy risks, ethical concerns, vulnerabilities, threat modeling, code analysis, fuzzing, and more.
2025-AI-College-Jobs
2025-AI-College-Jobs is a repository containing a comprehensive list of AI/ML & Data Science jobs suitable for college students seeking internships or new graduate positions. The repository is regularly updated with positions posted within the last 120 days, featuring opportunities from various companies in the USA and internationally. The list includes positions in areas such as research scientist internships, quantitative research analyst roles, and other data science-related positions. The repository aims to provide a valuable resource for students looking to kickstart their careers in the field of artificial intelligence and machine learning.

Prompt-Engineering-Holy-Grail
The Prompt Engineering Holy Grail repository is a curated resource for prompt engineering enthusiasts, providing essential resources, tools, templates, and best practices to support learning and working in prompt engineering. It covers a wide range of topics related to prompt engineering, from beginner fundamentals to advanced techniques, and includes sections on learning resources, online courses, books, prompt generation tools, prompt management platforms, prompt testing and experimentation, prompt crafting libraries, prompt libraries and datasets, prompt engineering communities, freelance and job opportunities, contributing guidelines, code of conduct, support for the project, and contact information.
cheat-sheet-pdf
The Cheat-Sheet Collection for DevOps, Engineers, IT professionals, and more is a curated list of cheat sheets for various tools and technologies commonly used in the software development and IT industry. It includes cheat sheets for Nginx, Docker, Ansible, Python, Go (Golang), Git, Regular Expressions (Regex), PowerShell, VIM, Jenkins, CI/CD, Kubernetes, Linux, Redis, Slack, Puppet, Google Cloud Developer, AI, Neural Networks, Machine Learning, Deep Learning & Data Science, PostgreSQL, Ajax, AWS, Infrastructure as Code (IaC), System Design, and Cyber Security.

Awesome-LLM4Cybersecurity
The repository 'Awesome-LLM4Cybersecurity' provides a comprehensive overview of the applications of Large Language Models (LLMs) in cybersecurity. It includes a systematic literature review covering topics such as constructing cybersecurity-oriented domain LLMs, potential applications of LLMs in cybersecurity, and research directions in the field. The repository analyzes various benchmarks, datasets, and applications of LLMs in cybersecurity tasks like threat intelligence, fuzzing, vulnerabilities detection, insecure code generation, program repair, anomaly detection, and LLM-assisted attacks.
LLMEvaluation
The LLMEvaluation repository is a comprehensive compendium of evaluation methods for Large Language Models (LLMs) and LLM-based systems. It aims to assist academics and industry professionals in creating effective evaluation suites tailored to their specific needs by reviewing industry practices for assessing LLMs and their applications. The repository covers a wide range of evaluation techniques, benchmarks, and studies related to LLMs, including areas such as embeddings, question answering, multi-turn dialogues, reasoning, multi-lingual tasks, ethical AI, biases, safe AI, code generation, summarization, software performance, agent LLM architectures, long text generation, graph understanding, and various unclassified tasks. It also includes evaluations for LLM systems in conversational systems, copilots, search and recommendation engines, task utility, and verticals like healthcare, law, science, financial, and others. The repository provides a wealth of resources for evaluating and understanding the capabilities of LLMs in different domains.
Awesome-AI-Security
Awesome-AI-Security is a curated list of resources for AI security, including tools, research papers, articles, and tutorials. It aims to provide a comprehensive overview of the latest developments in securing AI systems and preventing vulnerabilities. The repository covers topics such as adversarial attacks, privacy protection, model robustness, and secure deployment of AI applications. Whether you are a researcher, developer, or security professional, this collection of resources will help you stay informed and up-to-date in the rapidly evolving field of AI security.
go-cyber
Cyber is a superintelligence protocol that aims to create a decentralized and censorship-resistant internet. It uses a novel consensus mechanism called CometBFT and a knowledge graph to store and process information. Cyber is designed to be scalable, secure, and efficient, and it has the potential to revolutionize the way we interact with the internet.
TI-Mindmap-GPT
TI MINDMAP GPT is an AI-powered tool designed to assist cyber threat intelligence teams in quickly synthesizing and visualizing key information from various Threat Intelligence sources. The tool utilizes Large Language Models (LLMs) to transform lengthy content into concise, actionable summaries, going beyond mere text reduction to provide insightful encapsulations of crucial points and themes. Users can leverage their own LLM keys for personalized and efficient information processing, streamlining data analysis and enabling teams to focus on strategic decision-making.
beelzebub
Beelzebub is an advanced honeypot framework designed to provide a highly secure environment for detecting and analyzing cyber attacks. It offers a low code approach for easy implementation and utilizes virtualization techniques powered by OpenAI Generative Pre-trained Transformer. Key features include OpenAI Generative Pre-trained Transformer acting as Linux virtualization, SSH Honeypot, HTTP Honeypot, TCP Honeypot, Prometheus openmetrics integration, Docker integration, RabbitMQ integration, and kubernetes support. Beelzebub allows easy configuration for different services and ports, enabling users to create custom honeypot scenarios. The roadmap includes developing Beelzebub into a robust PaaS platform. The project welcomes contributions and encourages adherence to the Code of Conduct for a supportive and respectful community.
Nano
Nano is a Transformer-based autoregressive language model for personal enjoyment, research, modification, and alchemy. It aims to implement a specific and lightweight Transformer language model based on PyTorch, without relying on Hugging Face. Nano provides pre-training and supervised fine-tuning processes for models with 56M and 168M parameters, along with LoRA plugins. It supports inference on various computing devices and explores the potential of Transformer models in various non-NLP tasks. The repository also includes instructions for experiencing inference effects, installing dependencies, downloading and preprocessing data, pre-training, supervised fine-tuning, model conversion, and various other experiments.
specification
OWASP CycloneDX is a full-stack Bill of Materials (BOM) standard that provides advanced supply chain capabilities for cyber risk reduction. The specification supports various types of Bill of Materials including Software, Hardware, Machine Learning, Cryptography, Manufacturing, and Operations. It also includes support for Vulnerability Disclosure Reports, Vulnerability Exploitability eXchange, and CycloneDX Attestations. CycloneDX helps organizations accurately inventory all components used in software development to identify risks, enhance transparency, and enable rapid impact analysis. The project is managed by the CycloneDX Core Working Group under the OWASP Foundation and is supported by the global information security community.
airi
Airi is a VTuber project heavily inspired by Neuro-sama. It is capable of various functions such as playing Minecraft, chatting in Telegram and Discord, audio input from browser and Discord, client side speech recognition, VRM and Live2D model support with animations, and more. The project also includes sub-projects like unspeech, hfup, Drizzle ORM driver for DuckDB WASM, and various other tools. Airi uses models like whisper-large-v3-turbo from Hugging Face and is similar to projects like z-waif, amica, eliza, AI-Waifu-Vtuber, and AIVTuber. The project acknowledges contributions from various sources and implements packages to interact with LLMs and models.